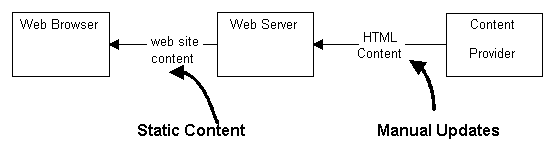
Figure 1: Data Flows of First-Generation Web Application
Kenneth W. Copeland <[email protected]>
U.S. Department of Veterans Affairs
USA
C. Jinshong Hwang <[email protected]>
Southwest Texas State University
USA
This paper is a short discussion of the required elements of the fully integrated business model that will be necessary for obtaining the highest efficiency in electronic commerce.
Electronic data interchange (EDI) has been around about as long as the Internet. Intranets and Web applications, however, are still relatively new terminology. Both terms, intranet and Web application, have gained widespread usage over the past couple of years. Each of the terms represent technological approaches to business applications and each of the technological approaches are steadily gaining converts. In the opinion of the authors, in order to take full advantage of the opportunities Internet connectivity offers to business, all three of these technological approaches to accomplishing business requirements will need to be integrated into a single, fully integrated computer operation.
As businesses get their feet wet on the Internet and begin building informational Web sites, one of the first problems encountered is that maintenance of Web pages is very tedious and labor intensive. Web applications are evolving and this evolution will soon allow for easier maintenance of these vital applications.
The initial activity for an organization getting onto the Internet is developing an informational Web page. This first-generation activity allows for the business to post information publicly to allow anyone with a Web browser and Internet access to view the business's information.
The problem with the first-generation Web application is that the information is static. Fixed content on the Web site means more activity on the part of users to find what they are looking for. Fixed content also requires changing the HTML formatting on the page itself in order to update the content. On Web sites containing a lot of content, this becomes an expensive proposition because the work is slow and labor intensive. Figure 1 shows the data flows for a typical first-generation Web application.

Figure 1: Data Flows of First-Generation Web Application
As can be see in figure 1. The manual, labor-intensive updates produce static information to the user.
The next level of activity involves allowing users to do interactive queries against existing databases from the Web application. These second-generation Web applications are more useful in presenting information to the user because the user can query the database for the content required. Used in conjunction with the content already provided in the informational Web site, the interaction between the user and the database increases the usefulness of the Web application to the user. Figure 2 shows the data flows for a typical second-generation Web application.
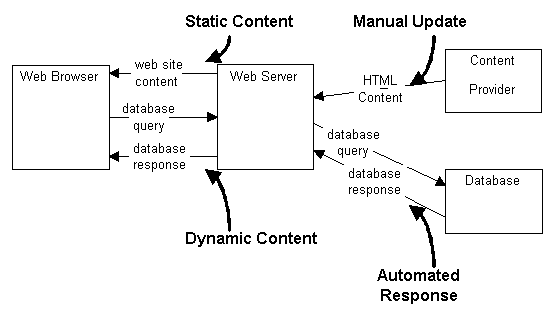
Figure 2: Data Flows of Second-Generation Web Application
This dynamically provided content, of the user's choosing, is updated by feeding the database, not by reformatting the Web page. This property of the second-generation Web application allows for the increased dynamic content to be provided with little change to the Web application itself. The changes that are required on the Web application are not as frequent as with the first-generation Web application.
The third-generation Web application allows databases to feed dynamic content to static HTML formats as the content changes (Copeland, 1996). Organizations have a need to make available new and changed information on a daily basis. Third-generation applications are more useful than second-generation applications, dynamically providing changing content to users. In combination with the query capabilities of the second-generation Web application and the static information provided by the first-generation Web application, the third-generation Web application is a powerful business tool for organizations in their electronic commerce (EC) efforts.
Applications with daily content changes usually create maintenance nightmares for the maintaining organization. Dynamically feeding the content from the database to the Web application alleviates the need for formatting the content after the creation and then uploading the formatted content to the Web site. The maintenance required on the third-generation Web application is limited to infrequent changes in the static content. Once the static content is in final form, maintenance is done from the database. Use of databases with user-defined attributes allows for the dynamic pushing of content onto the Web application from the database by using the Web applications as a pass-through area between the user and the database. Figure 3 shows the data flows of a typical third-generation Web application.
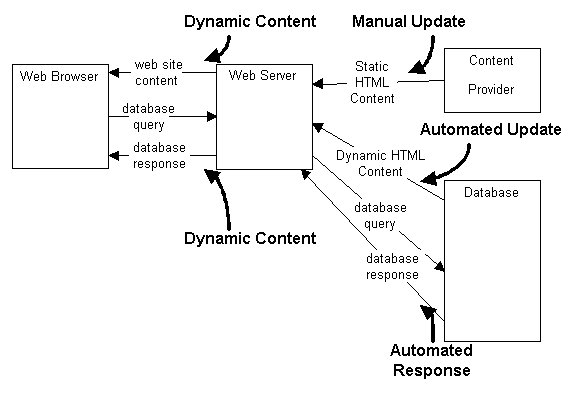
Figure 3: Data Flows of Third-Generation Web Application
As depicted in figure 3, all of the content to the user is dynamically created. This is a much more useful environment for business in its quest for relevance on the Internet and allows businesses to make efficient use of their Web sites.
All the hype about intranets is not unfounded. Business is finding that internal use of Web technologies is allowing fantastic returns on investments (Campbell, 1996) while leveraging existing applications.
Intranet is a fairly new term, not existent three or four years ago. It wasn't until Mosaic and the World Wide Web (Web), that the term started being used. The term has caught on and is one of the latest and most-used buzzwords in the computer and networking industries.
What does the term intranet really mean? When did intranets first exist? These are curious questions that lead to interesting discussions, but therein lies a problem. Although the terminology is being widely embraced, confusion as to what is meant can create problems when resources are sought for building this infrastructure.
Although the term intranet is new, some in the networking community say intranets have been around a very long time. What they are referring to is TCP/IP networks with restricted access. This definition of intranet, be it true or not, impedes the ability of some organizations to quickly employ a full-service intranet on top of existing wide area networks already supporting TCP/IP connectivity. The necessary resources to make it happen are not forthcoming because management knows it already has an enterprise-wide intranet.
For the purposes of this discussion, an intranet is not about connectivity and protocols, although those are prerequisites, but about services that are provided to the organization on top of the connectivity and protocols. The networks and connectivity were created by giants and it is now time to stand tall on their shoulders by extending their creation.
Web technology in and of itself offers considerable benefits as has been previously documented. (Bernard, 1996):
As noted earlier, the prerequisite for building an intranet, as the term is used in this discussion, is TCP/IP connectivity over a network with GUI interface support in the form of Web-client software.
Intranets, as the term is used here, require connectivity. But they are not about connectivity; they are about services. Forrester Research first explored the concept of a full-service intranet in a report titled "The Full Service Intranet," dated March 1, 1996 (Forrester, 1996). Simply put, a full-service intranet is a TCP/IP network inside an organization that links the organization's people and information in a way that makes people more productive, information more accessible, and navigation through all the resources and applications of the organization's computing environment more seamless than ever before.
The full-service intranet model is described in terms of services, which can be broken into two groups: user services and network services. Netscape Communications Corporation has done a good job of defining these services in their own intranet vision statement (Netscape, 1996).
User services are meant to provide resources and applications for the end users of the Intranet.
This service allows for the easy creation and publishing of documents online. Everyone with access rights has the latest information from anywhere on the network. Web documents are created using intuitive "what you see is what you get" (WYSIWYG) and drag-and-drop interfaces. Legacy document formats such as word processing documents and spreadsheets can be easily published. Documents are indexed and organized as they are published, and can be managed from the desktop, within the department, and centrally in one location. The result is a single, seamless environment for all information throughout the organization.
E-mail and groupware are ubiquitous on the Intranet. Access control and security allow both e-mail and discussion groups to be private, with all parties authenticated across the network. Transparent calendaring and scheduling provide a seamless collaboration environment. Users can look up e-mail addresses, security keys, and Internet phone numbers by using a simple address book interface tied into an open directory service across the Internet.
The full-service intranet makes it easy to find any piece of information or resource located on the network. Users can execute a single query that results in an organized list of all matching information from all servers throughout the organization. Indices and browsing hierarchies are easily created and maintained. With agent services, users can have servers watch for new information or monitor existing resources for changes. Access control allows only authorized users to have any level of access to restricted documents. Consequently, all users have comprehensive and personalized access to all important information across both their internal network and the Internet.
Existing databases, data warehouses, and legacy applications can be accessed easily from a single interface. New applications can be authored once with JavaScript and Java and quickly deployed on any platform, across all desktop and server operating environments and hardware platforms; all client-side application logic is downloaded when an application is accessed and the logic is automatically updated. Applications can be interwoven with content and can be deployed transparently over the Internet as well as over the internal Intranet. All the full-service intranet services are available to applications, including content management, directories, and replication. Application access can be easily controlled and can be built on top of business processes.
Network services are necessary to tie together and run the overall network environment from a centrally managed point.
Directory services track and manage information about people, access control, server configurations, and application-specific resources. The industry standard Lightweight Directory Access Protocol (LDAP) directory protocol breaks the proprietary directory bottleneck--directory services are seamless across all operating environments and applications on the intranet and Internet. End users can discover information about people, including e-mail addresses, security keys, and phone numbers. Administrators can centrally manage access control and server configuration parameters across the entire organization. Directory information can be replicated across the entire organization, enabling features such as universal single login.
The full-service intranet's security services provide ways for resources to be protected against unauthorized users, for communication to be encrypted and authenticated, and for the integrity of information to be verified. Web pages, directories, discussion groups, and databases are all subject to access control. This is managed centrally, with information about specific resources and about user privileges linked to those resources managed and distributed through the intranet's directory service. E-mail and real-time communication can be secured, with each party authenticated and with message traffic encrypted. Organizations can issue and manage a security key infrastructure to give their employees the ability to conduct company business securely across the network. Additionally, intranet applications can be extended securely across the intranet.
Replication maximizes the efficiency of the network by allowing data such as Web content, discussion group messages, directories, and database tables to be distributed across the intranet. Replication also makes it easy to take network resources such as discussion groups and directories off line in a way that allows the user to continue to make changes and updates; when the user goes back online, all the changes are properly reconciled.
The full-service intranet provides a common, integrated, user-friendly HTML-based management interface that allows all servers and resources to be managed securely from anywhere on the intranet. All full-service intranet servers support the Simple Network Management Protocol (SNMP). Directory services allow centralized, replicated, secure management of user information, access control parameters, and server configuration information, complete with one-button user account creation, deletion, and modification across the entire enterprise. Applications can integrate cleanly with any of these management foundations.
Besides supplying infrastructure for Web applications by providing a natural developmental and staging area for these applications, intranets have become so useful that they are now generally recognized as being necessary even if the organization has no need for Internet applications.
The first application that always comes to mind for intranets in and of themselves is the publication and distribution of documents. This application allows for paperless publication of any business information that is needed for internal employees or external customers or suppliers. Any type of document may be published on an intranet: policy and procedure manuals, employee benefits, software user guides, online help, training manuals, vacancy announcements--the list goes on to include any company documentation.
In the past it has not been easy to share electronic resources across network nodes. Employees have had problems sharing information for various reasons including software version inaccuracies and incompatibilities. Intranets provide the means to catalog resources online for easy deployment across the network to any authorized user with the click of a mouse. Software applications, templates, and tools are easily downloaded to any machine on the network.
Two-way communications and collaboration on projects, papers, and topics of interest become easy across the intranet. Types of communications that are enhanced and facilitated include e-mail, group document review, and use of groupware for developing new products.
Even though organizational full-service intranets are the next step in enterprise-wide computing and have enough value to make them desirable simply for the organizational benefits they bring, they are also necessary for supporting any Internet applications that are built.
The transactional processes and trading of information that will be done by all but the most elementary Web applications will require an infrastructure to store, move, and make use of the information that is traded. The infrastructure to accomplish those tasks is the organizational intranet.
The development and maintenance of the Internet application requires that the organization has a developmental environment and the means to test the applications prior to placing them on the Internet. This requires an intranet that mirrors the functionality of the Internet. The infrastructure also requires that the Internet application be easily updated and maintained by the staff that has the responsibility for the application. The infrastructure becomes even more important until the middleware to easily manage Internet applications becomes available. Because both intranet and Web application tools are still missing, maintenance on Internet applications will remain labor intensive for the next 18-24 months. This requires an infrastructure that allows easy access and manipulation by these labor-intensive processes.
Traditional EDI applications are very cost effective and these applications can be leveraged through the use of Web interfaces into the EDI applications and the databases that house the EDI data (Copeland, 1996). The new technologies do not propose to replace these applications, but to extend them. These traditional EDI applications are embellished, allowing the EDI user the capability to enhance the enterprise-wide EDI applications and trade information with non-EDI-enabled trading partners.
The EDI working groups of the IETF have been working to build interoperability standards so that the EDI can be effectively used over the Internet. The recent success of the CommerceNet pilots in this regard hold great promise that vendors with competing products will be able to have those products interact with each across the Internet. As the security of EDI transactions becomes assured and organizations begin to understand the Internet better, EDI over the Internet will offer real cost benefits in comparison to traditional EDI through VAN services.
The organization that builds the full-service intranet as organizational infrastructure today will have a solid foundation for EC tomorrow. All of the projected flow of business information and data across the Internet needs to be used electronically once it reaches the organization. Intranet infrastructure will allow data flow to continue on into the organizational applications and databases, rather than bottlenecking in a storage place until the data can be used internally.
Leveraging existing EDI applications and databases by supplying trading partner data from non-EDI vendors through the use of Web sites will further automate the efforts of the business and at the same time enhance the business presence on the Internet. Allowing trading partners to input and maintain their trading partner profiles and send and receive their business transactions electronically will greatly reduce time frames and increase efficiency with non-EDI trading partners.
Thus, building Web applications that can be fed content dynamically from databases will allow the programming effort to concentrate on backend processes. Keeping the backend processes tied electronically to data that is generated from both the EDI and non-EDI trading partners is critical to fully automated processes.
Web applications and intranets are the latest buzzwords, but they offer little utility. Used in the manner described in this paper, these two words are changed from buzzwords with little utility to powerful tools used for accomplishing EC. In contrast, EDI is well established and when integrated into the organizational backend processes, becomes the accomplishment of paperless business transactions between organizations. Mapping non-EDI inputs into existing EDI applications by capturing the input on a Web form allows the same paperless, backend processing to be accomplished with the non-EDI trading partner.
If the goal of the fully automated organization is to achieve the greatest efficiency at the least cost, these three methodologies need to be tied into backend processes that feed the data to databases. The stored data will then be used to feed other processes, all in an automated manner. This total integration between the databases, the EDI processes, the intranet applications, and the Internet applications will bring EC fully into the 21st century.
As process-to-process transactions across the Internet become a reality and database-to-database transactions across the Internet occur, EC on the Internet will begin to achieve the promise held out for it. The ideal model for the future will be simpler than today's and will resemble figure 4.
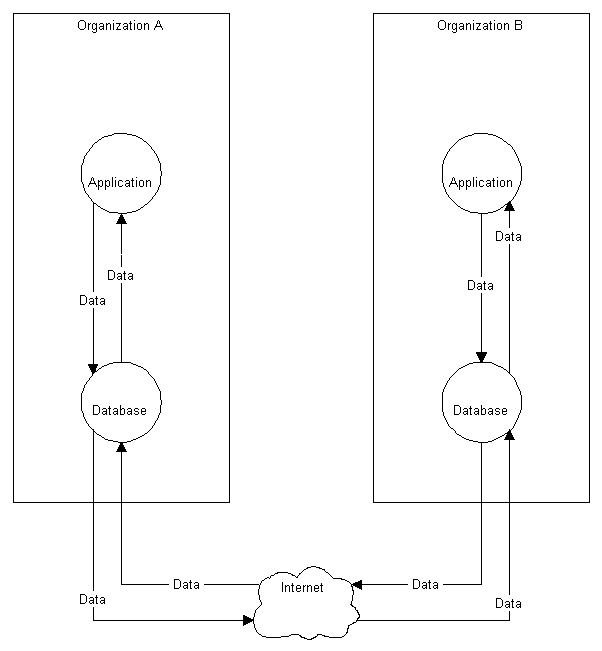
Figure 4: Model for Future Electronic Commerce Between Organizations
Bernard, R. (May 1996). Building a corporate intranet: How to use Internet tools to bring the information superhighway in-house. [Online] 24 pages. Available HTTP: http://www.Webcom.com/wordmark/sem_1.html [9 July 1996].
Campbell, I. (October 1996). Preliminary Report--The intranet: Slashing the cost of business. [Online] 22 pages. Available HTTP: http://cgi.netscape.com/cgi-bin/roi_reg.cgi [17 October 1996].
Copeland, K. W. (1996). Streamlining procurement through electronic commerce: An Internet approach for small purchases. Unpublished master's thesis, Southwest Texas State University, San Marcos, Texas.
Forrester Research (1 March 1996). The full-service intranet. The Forrester Report: Network Strategy Service (Volume Ten, Number Four), [Online] 13 pages. Available HTTP: http://www.forrester.com/hp_mar96nsr.htm [26 June 1996].
Netscape Communications Corporation (June 1996). The Netscape intranet vision and product roadmap. Version 1.0 [Online] 49 pages. Available HTTP: http://home.netscape.com/comprod/at_work/white_paper/intranet/vision.html [14 June 1996].